The New Method
Ragnar Locker ransomware group has a previous track record of targeting entities, rather than Individuals. This gang has recently hit Energias de Portugal (EDP), and stole 10TB worth data for a ransom price of 1,580 Bitcoin! Ragnar Locker ransomware carefully selects its targets, mostly corporates and governments, and crafts customized malware accordingly. This is to scrape the lumpsum payments in hundreds of thousands of dollars rather than petty tips from home users. And this ransomware has evolved with a new trick to hide better. This is by using Oracle’s old VirtualBox software! As a cybersecurity firm, Sophos revealed, Ragnar Locker group was found to be shifting its focus to Virtual Boxes, away from Windows RDP, Managed Service Provider, PowerShell, etc as in past attacks.
How Does It Do?
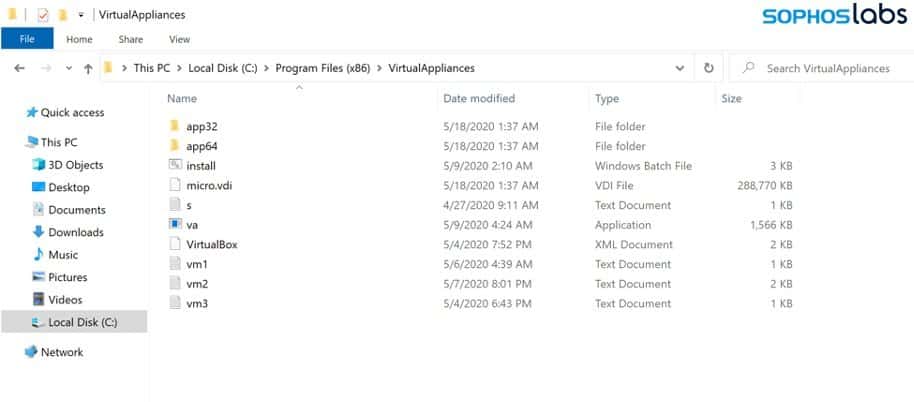
It all starts with picking a target computer and installing the Microsoft Installer via Windows Group Policy Objectives (GPOs). This lets the group to bypass security parameters, and to procure and install an unsigned MSI package from a remote web server. This package has the old Oracle VirtualBox hypervisor and a virtual disk image file of Windows XP SP3 OS. This is a stripped-down version of it and called MicroXP v0.82. This image also contains a 49 kB worth Ragnar Locker ransomware executable! This was installed inside the Oracle VirtualBox to avoid detection, as antivirus reads the actions performed within Virtual Box are from legitimate Oracle software, thus deemed to be safe. This software has access to all the local and shared disks, giving the hacker access to all of them to exfiltrate. Researchers say this is the first time a ransomware group found exploiting Virtual Box for its operations. Source: Sophos