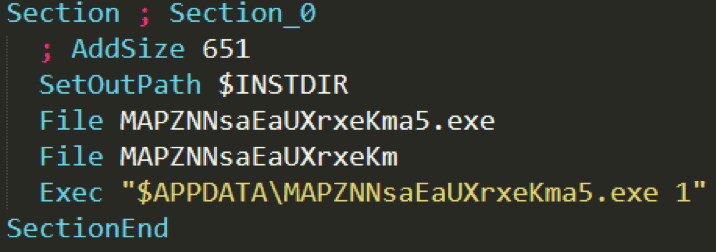
LokiBot was active since 2015, but only as a simple info stealer sneaking through exploiting the Remote Desktop Protocol (RDP) of systems. But now, it’s primarily targeted through phishing email campaigns and execute the malware to frame a backdoor. The data it steals contains sensitive credentials of cryptocurrency wallets, passwords, usernames, bank details etc.
Under the name of Epic Games!
And today, this malware trojan is effectively exploiting vulnerable gaming people under the name of popular game maker – Epic Games, owner of one of the popular games, Fortnite. Here, as reported by Trend Micro, LokiBot hackers are targeting users with phishing email campaign under as an Epic game Installer. The software launcher it’s promising is a potential malware that when downloaded, can infect and steal sensitive data from the system. Users are often warned not to install any softwares from untrusted sources, yet, falling for the game craze makes them install anything seemed attractive or cheap. After being downloaded (as attachments in email), it drops two files as C# and .NET in the app directory of system. After which, the .NET compiles the C#, which eventually dumps the LokiBot malware. The .NET executable was a highly obfuscated code, just included to make the reverse engineering hard. At last, the LokiBot cleverly evades the flagging softwares that only search the download binaries, and start stealing information and sending to the attacker. This malware trojan was named as Trojan.Win32.LOKI by Trend Micro and has the potential to innovate even further by ace hackers to make it harder to detect. Source: Trend Micro